Sandbox:OX Tutorial 100K/sandbox
Tutorial: High Available OX AppSuite Setup for up to 100.000 users
This article describes what you need for a typical OX AppSuite Setup for up to 100.000 Users, which is fully clustered and high available.
It contains everything you need to:
- Understand the design of the OX AppSuite setup including additional services
- Install the whole system based on the relevant articles
- Find pointers to the next steps of integration
System Design
High Level System Design
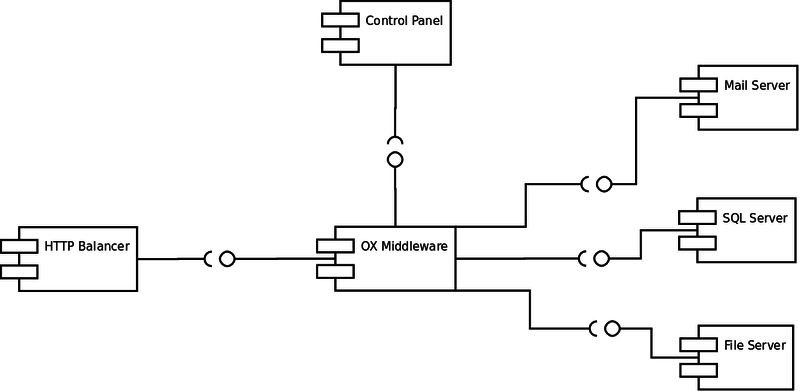
The overview shows that our OX AppSuite system will consist of several components:
- HTTP Balancer
- Accepts user requests and decides which part of the OX Middleware should handle them
- OX Middleware
- The central logic layer that handles the incoming requests
- Control Panel
- Used for creation and administration of users (not delivered by OX)
- Mail Server
- Used by the middleware to receive and send e-mails (not delivered by OX)
- SQL Server
- Used by the middleware to e.g. store pim objects
- File Server
- used by the middleware to store documents and files
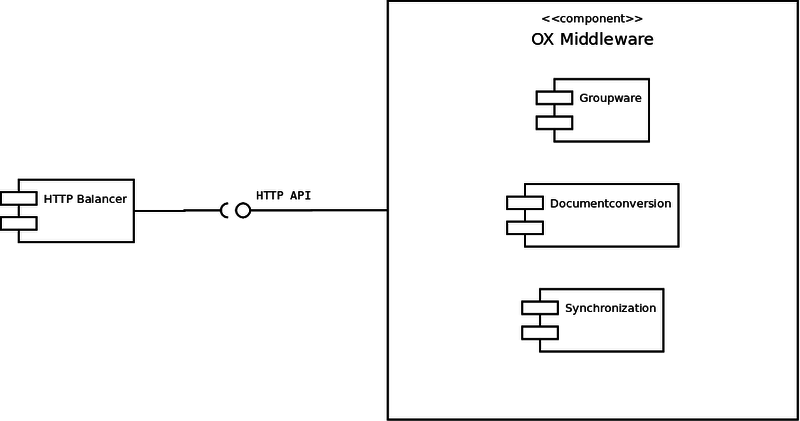
Middleware Details
The middleware itself consists of many modules whose functionality is either exposed via the HTTP_API or used internally. We have identified three blocks that should be grouped together and considered as logical components when planning the hardware layout and sizing of your infrastructure.
- Groupware
- definiton
- Documentconversion
- definition
- Synchronization
- definition
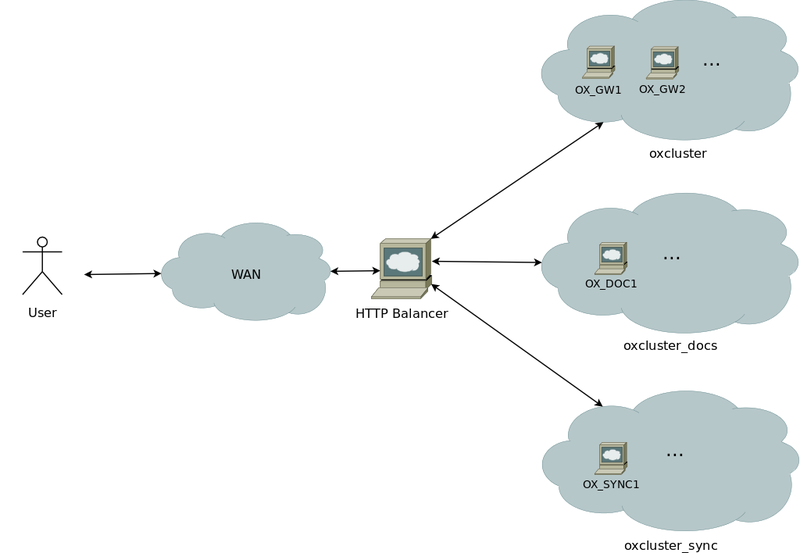
Component mappings in HTTP Balancer
The logical components mentioned above can be found again in our default Apache configuration which is distributed as part of the open-xchange-core package and located at /usr/share/doc/open-xchange-core/exapmples/proxy_http.conf.gz
You can find the wikified version at AppSuite:Grizzly#Apache_configuration
For each of the components we set up a balancing Proxy container so you can scale each of those components according to the number and demands of your users.
- Proxy balancer://oxcluster
- The members of this balancer container are responsible for handling general groupware requests
- Proxy balancer://oxcluster_docs
- The members of this balancer container are responsible for handling document conversion and thumbnailing requests
- Proxy balancer://oxcluster_sync
- The members of this balancer container are responsible for handling only USM, EAS and DAV synchronization requests
Specific Sizing Recommendations
Load Balancing
No Loadbalancer is needed in front of the default balancing HTTP server.
Middleware
Can we realistically offer to host 10k mailboxes on a single server?
Groupware
1..x groupware hosts with *specific hardware requirements*
Documentconversion
1..x conversion hosts with *specific hardware requirements*
Synchronisation
1..x sync hosts with *specific hardware requirements*
Mail Server
Standalone or on one of the middleware hosts?
SQL Server
Single master or replicated? Standalone or on one of the middleware hosts?
File Server
Standalone or on one of the middleware hosts?
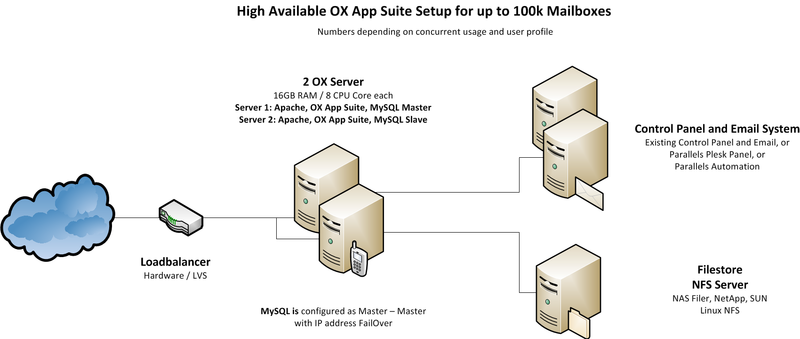
System Design
The system is designed to provide maximum functionality and availability with a minimum of necessary hardware. If the services on one server fail, it is enough to take over the IP address to the other machine and service will stay up and running.
Core Components for OX AppSuite
- Two OX AppSuite servers (HW recommendation: 16GB RAM / 4 cores each)
- MySQL installed directly on these server
- NFS Server to store documents and files
Infrastructure Components not delivered by OX
- An email system providing IMAP and SMTP
- A control panel for creation and administration of users
- A Load Balancer in front of the OX servers (optional, recommended)
Overview Installation Steps
To deploy the described OX setup, the following steps need to be done.
Mandatory Steps
- Initialize and configure MySQL database on both servers
- Install and configure OX on both servers
Steps depending on your environment
- Implement Load Balancer
- Connect Control Panel
- Connect Email System
Recommended Optional Next Steps
- Automated Frontend Tests (see here)
- Upsell Plugin (see here and here)
- Automatic FailOver
- Theming (see here)
Mandatory Installation Steps - Instructions & Recommendations
The following steps need to be done in every case to get OX up and running:
Initialize and configure MySQL database on both servers
MySQL will run on both servers. MySQL will be configured as Master-Master configuration to ensure data consistency on both servers. If one machine fails, the other machine will take over all functionality.
Database setup for clustered environments
Install and configure OX on both servers
OX will be installed on both servers. It will be configured to write to the first MySQL database and to read from the second MySQL database. This will distribute the load during normal operation as smooth as possible. During FailOver the IP address of the failed server will be taken over to the working server, the system stays operable.
Open-Xchange setup and configuration for clustered environments
The NFS server will be mounted on both machines and registered as filestore.
Filestore setup for clustered environments
When multiple Open-Xchange Servers are configured within a cluster Session and Loadbalancing needs to be set up.
Session and Loadbalancing for clustered environments
Network configuration for clustered environments
You also should install and configure the OXtender for Business Mobility
Installation of the OXtender for Business Mobility
Let your users connect to their data from other services like Twitter or LinkedIn by configuring the "SocialOX"
Installation Steps depending on your environment - Instructions & Recommendations
The following components need to be implemented in your environment.
Implement Load Balancer
A load balancer in front of the OX servers is recommended, but optional in this deployment size. (In small environments, DNS Round Robin may be sufficient).
If you already have a hardware load balancing solution in place, this can be used. OX is known to work with the standard load balancing solutions from BigIP, Barracuda, Foundry, ...
If you do not have a load balancing solution already in place, we recommend to use Keepalived as reliable and cost effective solution.
Read more about configuring Keepalived for Open-Xchange
Connect Control Panel
You need a Control Panel to create and edit users.
OX is designed to integrate into every solution you may already run in your environment and also into wide spread solutions, like the Parallels Control Panels.
If you do not run hosting services today and do not have a Control Panel in place, it is recommend to use Plesk to manage OX. With that combination you will get a full functional hosting platform containing everything you need.
Integrate your own Control Panel
If you already have a Control Panel in production, you should integrate OX with it. It is recommended to use the SOAP provisioning Interface for that purpose.
Read more about: Provisioning using SOAP
A good start to test and to understand the necessary commands are the Command Line Tools. They have exactly the same calls like the SOAP API.
Read more about: Open-Xchange CLT
Integrate with Parallels Automation (POA)
Parallels Operations Automation (POA) is an operations support system (OSS) for service providers, who want to differentiate their offerings in order to reduce customer churn and attract new customers. Additional, the APS package adds a high performance, best in class email service to Parallels Plesk Panel customers.
Authentication
To avoid password synchronization issues, it is recommended to use your existing email authentication mechanism within OX. Then you do not need to add user passwords to OX, you simply use a plugin to authenticate against your IMAP server.
Read more about the IMAP Authentication Plugin
Connect Email System
Every email system providing IMAP and SMTP can be used as backend to OX. Best experiences are made with the widespread Linux based IMAP servers Dovecot, Cyrus or Courier.
Other IMAP servers need to be tested thoroughly before going into production.
There are several possibilities to implement the Email system:
- You already have an email system available: Nothing needs to be done, it just needs to be configured
- You use Parallels Automation (POA): Nothing special needs to be done, everything you need is contained in the APS package
- You want to setup a new Email system: It is recommended to use Dovecot, as this is very stable, fast, feature rich and easy to scale
Dovecot Setup
If you want to setup a new Email system based on Dovecot, it is recommended to use NFS as storage backend and to install at least two Dovecot servers, accessing this storage. With that setup you have best scalability and high availability with a minimum of complexity and hardware.
Read more in the Dovecot documentation including a QuickConfiguration guide
Recommended Optional Next Steps
You will find plenty of additional documentation for customization of OX in our knowledge base [1]
When the main setup is completed, we recommend to start with the following articles to enhance your system and to become more attractive for your users.
Monitoring / Statistics
It is recommended to implement at least a minimal monitoring/Statistics solution to get an overview of the systems health. If you have a support contract with Open-Xchange, it is very helpful, if the support can access the monitoring graphs. There are example scripts for a basic monitoring with [Munin] available.
Read more about installing and configuring Munin scripts for Open-Xchange
Backup
It is recommended to run regular backups for your OX installation. This can be done with every backup solution for Linux.
Read more about Backup your Open-Xchange installation
IP FailOver
For automatic IP failover, several solutions are available for Linux. A reliable working framework is: