AppSuite:GoogleAppVerification: Difference between revisions
(Created page with "= Google App Verification = == Problem == Google has recently restricted the possibility to allow 3rd party developers to integrate their applications with Google services, s...") |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 2: | Line 2: | ||
== Problem == | == Problem == | ||
Google has recently restricted the possibility to allow 3rd party developers to integrate their applications | Google has recently again restricted the possibility to allow 3rd party developers to integrate their applications | ||
with Google services, see [https://support.google.com/cloud/answer/7454865 this article] for further information. In essence, a verification process was | with Google services, see [https://support.google.com/cloud/answer/7454865 this article] for further information. In essence, a verification process was | ||
introduced that requires multiple steps to be taken. This change affects all Google integrations for OX App | introduced and recently hardened that requires multiple steps to be taken. This change affects all Google integrations for OX App | ||
Suite: | Suite: | ||
* external mail accounts (if configured to use OAuth for Google) | * external mail accounts (if configured to use OAuth for Google) | ||
| Line 13: | Line 13: | ||
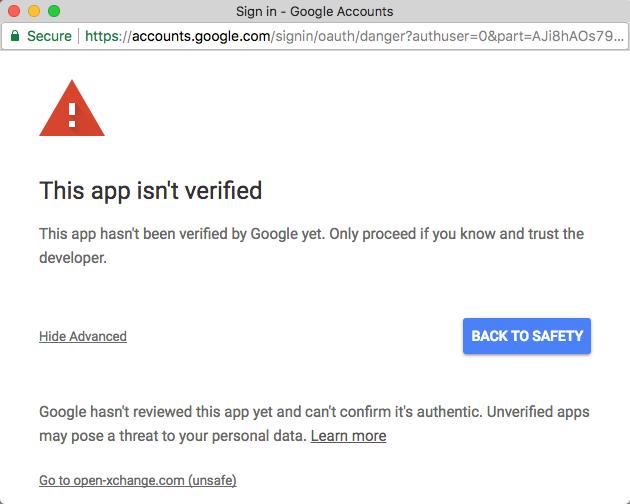
Without verification, users will see a warning message instead of a login form in the authorization popups. | Without verification, users will see a warning message instead of a login form in the authorization popups. | ||
While the warning itself can be ignored with some effort, also the number of users that might use a certain | While the warning itself can be ignored with some effort, also the number of users that might use a certain | ||
3rd party app with Google gets limited. | 3rd party app with Google gets limited. Current information for unverified Apps is apparently that they may stop working at least partially by March 31st 2019. | ||
[[File:google_verification_error.jpg]] | [[File:google_verification_error.jpg]] | ||
== Solution == | == Solution == | ||
The following is necessary to avoid the limitations: | The following is necessary to avoid the limitations: (also see [https://developers.google.com/apps-script/guides/client-verification#requesting_verification Google's documentation]) | ||
* In [https://console.developers.google.com/ Google Developer Console], ensure that the OAuth consent screen settings include a valid homepage URL and a publicly available privacy policy URL below the same domain. | * In [https://console.developers.google.com/ Google Developer Console], ensure that the OAuth consent screen settings include a valid homepage URL and a publicly available privacy policy URL below the same domain. | ||
* In [https://www.google.com/webmasters/tools/home Google Search Console], ensure that the homepage URL is a verified property of the Google account that is used to obtained the API keys. | * In [https://www.google.com/webmasters/tools/home Google Search Console], ensure that the homepage URL is a verified property of the Google account that is used to obtained the API keys. | ||
* Submit a verification request at Google | * Submit a verification request at Google. Please note that since latest changes to the process Google performs a security assessment on the respective infrastructure through a 3rd party provider (cited from Google's help pages): | ||
Assessments will be conducted by a Google-designated third party assessor, may cost between $15,000 and $75,000 (or more) depending on the complexity of the application, and will be payable by the developer. This fee may be required whether or not your app passes the assessment. | |||
You need to specify the following scopes in the verification form, depending on which functionality you do | You need to specify the following scopes in the verification form, depending on which functionality you do | ||
| Line 38: | Line 39: | ||
to use their respective Google account data from within our web | to use their respective Google account data from within our web | ||
application. | application. | ||
- Our | - Our OX App Suite uses scope " https://mail.google.com/" to obtain OAuth token | ||
to | pairs to access Gmail IMAP and SMTP via the XOAUTH2 SASL login mechanism. | ||
The application does not download and store any email data of Gmail users persistently. | |||
OX App Suite is a webmail application, commonly used by TelCos and ISPs, that offers | |||
email to end users. In addition to a provider-specific mailbox, users can include | |||
external email accounts like Gmail per IMAP and SMTP access into the web application. | |||
If a user adds a Gmail account to an OX App Suite webmail account, she can browse through | |||
folders and emails, read email contents incl. attachments (using IMAP under the hood) and | |||
send new emails per the Gmail SMTP server. | |||
- Scope https://www.googleapis.com/auth/contacts.readonly is used by our app | - Scope https://www.googleapis.com/auth/contacts.readonly is used by our app | ||
to let users import contacts from their Google address book. Imports are | to let users import contacts from their Google address book. Imports are | ||
| Line 57: | Line 63: | ||
It might happen that despite submitting the verification request, you get no positive answer even after | It might happen that despite submitting the verification request, you get no positive answer even after | ||
weeks. In that case please answer to the submit confirmation mail and ask for guidance on how to proceed | weeks. In that case please answer to the submit confirmation mail and ask for guidance on how to proceed | ||
to get your app verified | to get your app verified. | ||
Latest revision as of 14:19, 25 March 2019
Google App Verification
Problem
Google has recently again restricted the possibility to allow 3rd party developers to integrate their applications with Google services, see this article for further information. In essence, a verification process was introduced and recently hardened that requires multiple steps to be taken. This change affects all Google integrations for OX App Suite:
- external mail accounts (if configured to use OAuth for Google)
- calendar
- address book
- OX Drive storage integration
Without verification, users will see a warning message instead of a login form in the authorization popups. While the warning itself can be ignored with some effort, also the number of users that might use a certain 3rd party app with Google gets limited. Current information for unverified Apps is apparently that they may stop working at least partially by March 31st 2019.
Solution
The following is necessary to avoid the limitations: (also see Google's documentation)
- In Google Developer Console, ensure that the OAuth consent screen settings include a valid homepage URL and a publicly available privacy policy URL below the same domain.
- In Google Search Console, ensure that the homepage URL is a verified property of the Google account that is used to obtained the API keys.
- Submit a verification request at Google. Please note that since latest changes to the process Google performs a security assessment on the respective infrastructure through a 3rd party provider (cited from Google's help pages):
Assessments will be conducted by a Google-designated third party assessor, may cost between $15,000 and $75,000 (or more) depending on the complexity of the application, and will be payable by the developer. This fee may be required whether or not your app passes the assessment.
You need to specify the following scopes in the verification form, depending on which functionality you do offer. Unfortunately, every change of your offered feature set or changes by Open-Xchange might require re-verification in the future:
- https://mail.google.com/
- https://www.googleapis.com/auth/calendar.readonly
- https://www.googleapis.com/auth/contacts.readonly
- https://www.googleapis.com/auth/drive
Also, you need to provide an explanation why your instance of OX App Suite requires these scopes. A possible statement could be:
With [Product Name], we offer email, personal information management and a cloud storage solution. We want to offer our users the possibility to use their respective Google account data from within our web application. - Our OX App Suite uses scope " https://mail.google.com/" to obtain OAuth token pairs to access Gmail IMAP and SMTP via the XOAUTH2 SASL login mechanism. The application does not download and store any email data of Gmail users persistently. OX App Suite is a webmail application, commonly used by TelCos and ISPs, that offers email to end users. In addition to a provider-specific mailbox, users can include external email accounts like Gmail per IMAP and SMTP access into the web application. If a user adds a Gmail account to an OX App Suite webmail account, she can browse through folders and emails, read email contents incl. attachments (using IMAP under the hood) and send new emails per the Gmail SMTP server. - Scope https://www.googleapis.com/auth/contacts.readonly is used by our app to let users import contacts from their Google address book. Imports are periodically refreshed. The contacts are then used to make find-as-you-type suggestions when composing emails, creating appointments, etc. - We request scope https://www.googleapis.com/auth/calendar.readonly to let users import their appointments from Google Calendar into our own calendar application. Imports are periodically refreshed. The appointments can be viewed from within our web frontend. - The app uses https://www.googleapis.com/auth/drive to allow users to browse their Google Drive and manage files and folders. They also can select Google Drive files as attachments for emails that are composed with our webmail module.
It might happen that despite submitting the verification request, you get no positive answer even after weeks. In that case please answer to the submit confirmation mail and ask for guidance on how to proceed to get your app verified.