PowerDNS:PowerDNS Parental Malware Control: Difference between revisions
(Created page with "= PowerDNS Parental & Malware Control = PowerDNS safeguards your customers with multi-level access control for safe browsing using a combination of rock-solid PowerDNS server...") |
No edit summary |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= PowerDNS Parental & Malware Control = | = OX PowerDNS Parental & Malware Control = | ||
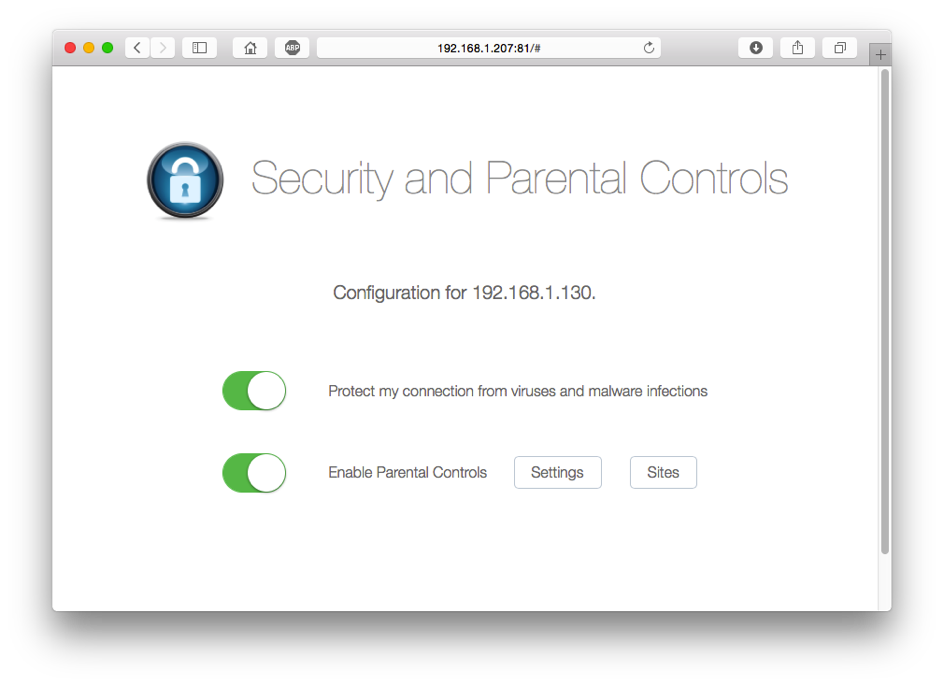
PowerDNS safeguards your customers with multi-level access control for safe browsing using a combination of rock-solid PowerDNS servers coupled withWeb filters that use categories to define which domains should be blocked for particular clients. In addition to categories, Parental Control supports time windows, white lists and black lists for fine-tuning access control. Features such as configurable NXDOMAIN redirection and an easy-to-use Web Control panel round up the offering. When used with appropriate CPE equipment with support for EDNS-client, Parental Control can decide based on the client’s IP address. | OX PowerDNS safeguards your customers with multi-level access control for safe browsing using a combination of rock-solid OX PowerDNS servers coupled withWeb filters that use categories to define which domains should be blocked for particular clients. In addition to categories, Parental Control supports time windows, white lists and black lists for fine-tuning access control. Features such as configurable NXDOMAIN redirection and an easy-to-use Web Control panel round up the offering. When used with appropriate CPE equipment with support for EDNS-client, Parental Control can decide based on the client’s IP address. | ||
[[Image:Malware_1.png]] | [[Image:Malware_1.png]] | ||
The PowerDNS Parental Control & Malware detection uses a combination of blindingly fast Constant Database (CDB) files, Response Policy Zones (RPZ) and a PostgreSQL database table from which it bases the policy to apply for DNS queries. We offer this to provide subscribers with the peace of mind that all devices on their network (including those they don’t understand or know about) are under control. | The OX PowerDNS Parental Control & Malware detection uses a combination of blindingly fast Constant Database (CDB) files, Response Policy Zones (RPZ) and a PostgreSQL database table from which it bases the policy to apply for DNS queries. We offer this to provide subscribers with the peace of mind that all devices on their network (including those they don’t understand or know about) are under control. | ||
For sensitive environments queries to search engines are redirected to 'safe search'. | For sensitive environments queries to search engines are redirected to ''safe search''. | ||
Thanks to the use of DNS resolution only, unfiltered domain names do not restrict devices | Thanks to the use of DNS resolution only, unfiltered domain names do not restrict devices in any way: normal DNS resolution proceeds, and applications are blissfully unaware of content protection, contrary to the use of, say, HTTP proxies, which do influence clients’ | ||
requirements. | |||
== How it works == | |||
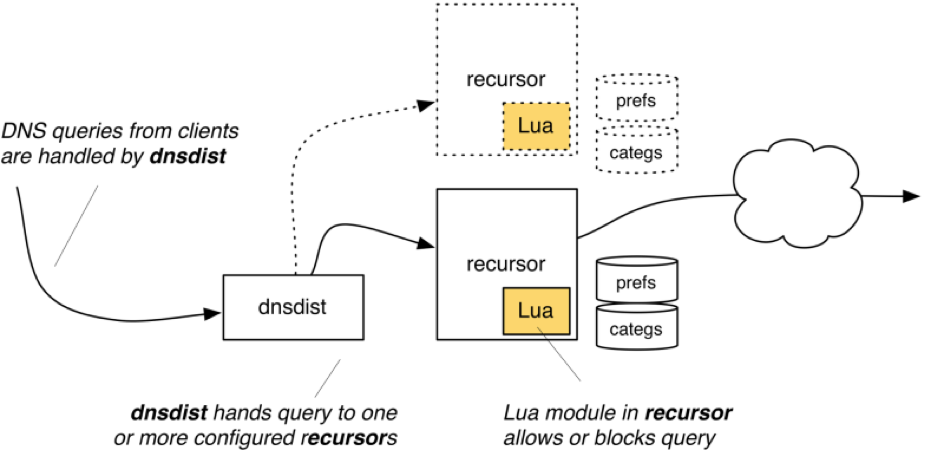
In very simple terms, a client application issues a DNS query for a particular domain. This query is intercepted by OX PowerDNS Parental and verified against its datasets. If it passes all controls, the DNS query is resolved and responses are returned to the clients. If access control fails, a unique configurable IP address of a Web filter is returned to the client. The client’s Web browser then connects to the Web filter which does more checks on the URL. If the filter grants access, the Web request is proxied to the origin, otherwise a page which explains why the query was blocked is displayed. | |||
[[Image:Malware_2.png]] | |||
The traditional “one world” view of a recursive name server no longer applies, and neither do the “inside/outside” views as used by other DNS name server implementations; OX PowerDNS Parental eliminates the need for complex configuration and huge amounts of RAM by providing dynamic lookups using configurable and customizable modules. | |||
== Why use it? == | |||
Whether in a huge corporate environment or in a family household, filtering of DNS queries should be done for a number of reasons: | |||
* Per-user filtering is a source of tension. (“Why is she allowed, and I’m not?”) | |||
* Per-device filtering is tedious and challenging to configure and verify | |||
* Prevents malware infections | |||
* Detects and warns users | |||
* Allows for long-term storage & logging of queries | |||
* Lawful interception and data retention may be mandatory | |||
In particular, when using the OX PowerDNS Parental security application, subscribers need not worry about their Internet security. In view of the fact that SOHO and SME are slowly becoming maintainer-less and thus do not have an “administrator” on site, the added level of protection for all devices (also future devices!) becomes important. | |||
The fact that users associate being safe from infections with the service offered by service providers, makes the OX PowerDNS Parental & Malware Control application useful to have. | |||
== Operation == | |||
As mentioned above, the individual components speak to each other, irrespective of whether they are installed on one or more machines. | |||
The basic premise is a client (for example a Web browser) which has the IP address(es) of one or more dnsdist processes configured as resolvers in its /etc/resolv.conf. The client DNS request is received by dnsdist which hands it over to the Recursor for doing the hard work of looking up the desired query. | |||
The Recursor utilizes the Lua hook scripts to query the CDB database in order to determine whether the desired domain name has been blocked, and if so, why. In the case of blockage, the Recursor returns to dnsdist a configured address of the Web filter, whereupon the Web browser will open a connection to this filter to be informed that the domain has been blocked for a particular reason. | |||
If the Recursor deems that the domain was not blocked, it performs recursion (over the Internet) to resolve the query, whereupon it returns, via dnsdist, this response to the requesting client. | |||
=== Verifying a blocked site === | |||
In order to verify that the Recursor and the Web filter are correctly blocking a particular | |||
site, you can use the manual query utility, passing it the domain name and the client’s IP address: | |||
$ /opt/parental/manualquery.lua example.org 192.168.1.207 | |||
time: Wed Jun 8 13:49:40 2016 | |||
decision: false | |||
categories: | |||
match point: example.org | |||
The decision specifies whether the decision to block is true or false. For example, using the IP address of a different client, i.e. one which has explicitly blocked the site, the output would be | |||
$ /opt/parental/manualquery.lua example.org 192.168.1.130 | |||
time: Wed Jun 8 13:53:03 2016 | |||
decision: true | |||
categories: -1 | |||
match point: example.org | |||
== Dynamic services == | |||
OX PowerDNS uses scriptable back-ends with hooks written in the Lua programming language to intercept queries and provide customer-definable responses based on policy decisions. | |||
These hook scripts can be modified and augmented to encompass any desired functionality, such as | |||
* additional logging | |||
* other data sources for blocking | |||
Latest revision as of 08:58, 2 December 2016
OX PowerDNS Parental & Malware Control
OX PowerDNS safeguards your customers with multi-level access control for safe browsing using a combination of rock-solid OX PowerDNS servers coupled withWeb filters that use categories to define which domains should be blocked for particular clients. In addition to categories, Parental Control supports time windows, white lists and black lists for fine-tuning access control. Features such as configurable NXDOMAIN redirection and an easy-to-use Web Control panel round up the offering. When used with appropriate CPE equipment with support for EDNS-client, Parental Control can decide based on the client’s IP address.
The OX PowerDNS Parental Control & Malware detection uses a combination of blindingly fast Constant Database (CDB) files, Response Policy Zones (RPZ) and a PostgreSQL database table from which it bases the policy to apply for DNS queries. We offer this to provide subscribers with the peace of mind that all devices on their network (including those they don’t understand or know about) are under control.
For sensitive environments queries to search engines are redirected to safe search.
Thanks to the use of DNS resolution only, unfiltered domain names do not restrict devices in any way: normal DNS resolution proceeds, and applications are blissfully unaware of content protection, contrary to the use of, say, HTTP proxies, which do influence clients’ requirements.
How it works
In very simple terms, a client application issues a DNS query for a particular domain. This query is intercepted by OX PowerDNS Parental and verified against its datasets. If it passes all controls, the DNS query is resolved and responses are returned to the clients. If access control fails, a unique configurable IP address of a Web filter is returned to the client. The client’s Web browser then connects to the Web filter which does more checks on the URL. If the filter grants access, the Web request is proxied to the origin, otherwise a page which explains why the query was blocked is displayed.
The traditional “one world” view of a recursive name server no longer applies, and neither do the “inside/outside” views as used by other DNS name server implementations; OX PowerDNS Parental eliminates the need for complex configuration and huge amounts of RAM by providing dynamic lookups using configurable and customizable modules.
Why use it?
Whether in a huge corporate environment or in a family household, filtering of DNS queries should be done for a number of reasons:
- Per-user filtering is a source of tension. (“Why is she allowed, and I’m not?”)
- Per-device filtering is tedious and challenging to configure and verify
- Prevents malware infections
- Detects and warns users
- Allows for long-term storage & logging of queries
- Lawful interception and data retention may be mandatory
In particular, when using the OX PowerDNS Parental security application, subscribers need not worry about their Internet security. In view of the fact that SOHO and SME are slowly becoming maintainer-less and thus do not have an “administrator” on site, the added level of protection for all devices (also future devices!) becomes important.
The fact that users associate being safe from infections with the service offered by service providers, makes the OX PowerDNS Parental & Malware Control application useful to have.
Operation
As mentioned above, the individual components speak to each other, irrespective of whether they are installed on one or more machines.
The basic premise is a client (for example a Web browser) which has the IP address(es) of one or more dnsdist processes configured as resolvers in its /etc/resolv.conf. The client DNS request is received by dnsdist which hands it over to the Recursor for doing the hard work of looking up the desired query.
The Recursor utilizes the Lua hook scripts to query the CDB database in order to determine whether the desired domain name has been blocked, and if so, why. In the case of blockage, the Recursor returns to dnsdist a configured address of the Web filter, whereupon the Web browser will open a connection to this filter to be informed that the domain has been blocked for a particular reason.
If the Recursor deems that the domain was not blocked, it performs recursion (over the Internet) to resolve the query, whereupon it returns, via dnsdist, this response to the requesting client.
Verifying a blocked site
In order to verify that the Recursor and the Web filter are correctly blocking a particular site, you can use the manual query utility, passing it the domain name and the client’s IP address:
$ /opt/parental/manualquery.lua example.org 192.168.1.207 time: Wed Jun 8 13:49:40 2016 decision: false categories: match point: example.org
The decision specifies whether the decision to block is true or false. For example, using the IP address of a different client, i.e. one which has explicitly blocked the site, the output would be
$ /opt/parental/manualquery.lua example.org 192.168.1.130 time: Wed Jun 8 13:53:03 2016 decision: true categories: -1 match point: example.org
Dynamic services
OX PowerDNS uses scriptable back-ends with hooks written in the Lua programming language to intercept queries and provide customer-definable responses based on policy decisions.
These hook scripts can be modified and augmented to encompass any desired functionality, such as
- additional logging
- other data sources for blocking